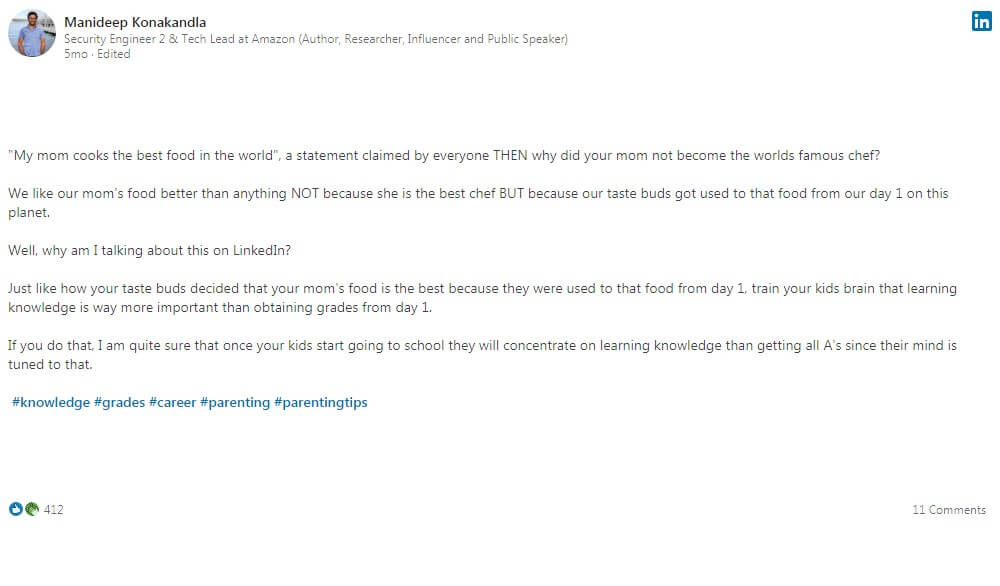
Author at OWASP CSRF Prevention Cheat sheet
Publication date: Oct 2018
Publication description: OWASP
Publication description: Author and Primary Editor for OWASP CSRF Prevention Cheat sheet
https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)_Prevention_Cheat_Sheet
https://www.owasp.org/index.php/OWASP_Cheat_Sheet_Series
Author at OWASP CSRF Prevention Cheat sheet
Publication title: How secure is your Docker Container pipeline?
Publication date: Feb 22, 2017
Publication description: Talk at Container World conference on docker container pipeline security
How secure is your Docker Container pipeline?
Publication title: Docker Images Security
Publication date: Feb 13, 2017
Publication description: Talk at BSides conference (San Francisco chapter) on Docker Images Security
Docker Images Security
Publication title: Is Docker Secure?
Publication date: Nov 18, 2016
Publication description: Container / Docker security in 30 minutes at Grehack'16 conference in France.
Is Docker Secure?
Publication title: Breaking and Fixing your 'Docker'ized environments
Publication date: Oct 14, 2016
Publication description: My talk at OWASP AppsecUSA 2016 conference (2016.appsecusa.org/)
Video: https://www.youtube.com/watch?v=wVIFdxgRCMM
Slidedeck: http://www.slideshare.net/manideepkofficial/breaking-and-fixingyourdockerizedenvironmentsowaspappsecusa2016
Breaking and Fixing your 'Docker'ized environments
Publication title: Cracking Barcodes
Publication date: Dec 15, 2014
Spoke about cracking barcodes in Security Conference - Hyderabad Chapter.
Cracking Barcodes
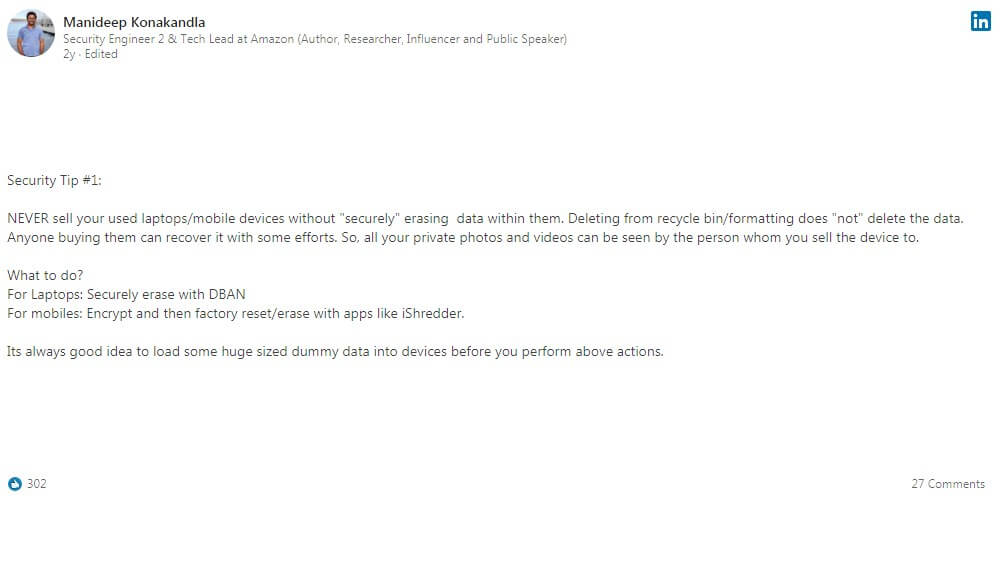
Publication title: Basics of Data Erasure - Information Security
Publication date: Nov 16, 2014
Publication description: http://www.slideshare.net/manideepkofficial/basics-of-secure-data-erasure-information-security
Basics of Data Erasure - Information Security
Publication title: A Complete Practical Guide to Ethical Hacking and Information Security
Publication date: Mar 5, 2012 publication descriptionScitech Publishers
Publication description: Book (Currently out of stock - 2nd version WIP).
Publication title: BOF on Yahoo Messenger
Publication date: Feb 6, 2012 publication descriptionSecurityFocus
Publication description: Brief video was published on this link. In-detailed technical analysis report link will be updated here soon
BOF on Yahoo Messenger
Publication title: CIS Docker benchmark 1.12 & 1.13
Publication description: Center for Internet Security (CIS)
Publication description: Co - author : https://benchmarks.cisecurity.org/downloads/show-single/index.cfm?file=docker12.100
Contributor: https://benchmarks.cisecurity.org/downloads/show-single/index.cfm?file=docker13.100
Publication title: CVE-IDs (Low critical) for reporting vulnerabilities in CMS's, WP Plugins etc.
Publication description: CVE-2014-8780, CVE-2014-9394 , CVE-2014-9396 , CVE-2014-9400 , CVE-2014-9392, CVE-2014-9336, CVE-2014-9337, CVE-2014-9338, CVE-2014-9339, CVE-2014-9391, CVE-2014-9368
CVE-2014-9398, CVE-2014-9401, CVE-2014-9341, CVE-2014-9340, CVE-2014-9334, CVE-2014-9335, CVE-2014-9393, CVE-2014-9395, CVE-2014-9399,CVE-2014-9397